Whispered %fuckbook.com% Secrets
Step-by-step Notes on Chinese Mail Order Brides In Detail by detail Order
9 أبريل، 2020Fast Methods In Cbd For Dogs – Insights
10 أبريل، 2020Whispered %fuckbook.com% Secrets
How To Avoid Losing Money To A Romance Scammer
As quickly as the “port out” completes, the phone quantity activates on an attacker’s SIM card, and the hacker can ship and obtain messages and make calls as in the event that they have been the individual they just hacked. Often, hackers will find the cellular phone number of their target floating across the internet (or from a telephone invoice in the garbage), and name up their provider impersonating the client. With a couple of easy questions answered — often little greater than the place a person lives or their date of delivery, they ask the customer service consultant to “port out” the phone number to a unique provider or a SIM card. Whether you’re an AT&T, Verizon, Sprint or T-Mobile buyer, every cellular phone number can be a goal for hackers.
In nearly any identity-theft state of affairs, a thief will need to have greater than your name and address to commit fraud. So these details could possibly be a gateway into your monetary world, however it’s not your last line of protection. Another attempt at theft offline contains “phishing,” which can be done via good old-fashioned snail mail. That’s when a faux entity sends you mail cleverly disguised as a respectable establishment requesting cash or financial info.
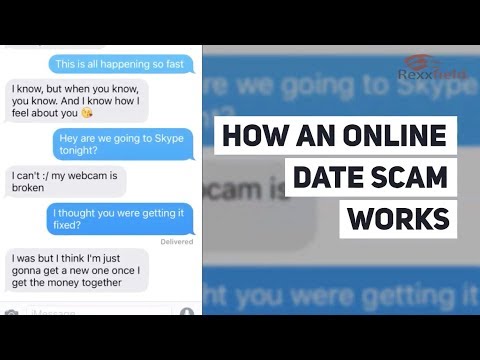
You could feel heartbroken, depressed, or embarrassed after somebody you trusted scammed you. But the scam artist will cancel on the last minute, providing an elaborate cause for why they can’t see you after is fuckbook safe all. Scammers sometimes work to maintain their identities secret. That’s because as soon as they’ve taken your cash, they don’t need to get caught.
Dating & Romance
You can both call up customer providers or do it on-line. Just like you’ll be able to apply two-issue authentication to your online accounts, you possibly can add a secondary security code to your cellular phone account, too. In most instances, the one sign that it happened is if the victim suddenly loses cell service for no obvious reason.
Inheritance Scams
In this new report, scientists used a Google-inspired algorithm to grasp the wishes of people wanting to match up. They analysed messaging and demographic patterns amongst heterosexual customers in New York, Boston, Chicago and Seattle. Norton 360™ with LifeLock™, all-in-one protection in opposition to evolving threats to your linked units, online privacy and id. More than 50 million clients belief Norton with their personal info. Besides the monetary costs, there may be emotional costs, too.
Keep your smartphone on you, or inside view, whereas in public. Use cellular security software program—These days your smartphone is just as data rich as your pc. Make certain to guard your critical data, and your privacy, by utilizing comprehensive mobile securitysoftware that not solely protects you from online threats, however provides anti-theft and privateness safety. If the issue still doesn’t go away, think about restoring your telephone to its authentic settings.
Identity thieves are all the time looking out for personally identifiable info, or PII, that they’ll use to start out piecing together an individual’s financial world. This can embrace particulars like Social Security quantity, birthdate, or name and address.
And it takes remarkably little effort to wreak havoc to your on-line life. Never leave your gadget unattendedin public—While many threats exist on-line, you still have to be aware of actual-world threats, like somebody grabbing your gadget if you’re not wanting.
The person’s messages appear to be they could possibly be copy-and-pasted into any dialog. They could possibly report inappropriate messages or offensive folks. And if they use inventory pictures for their profile picture or refuse to video chat?
Search on-line for instructions for your explicit cellphone and working system to learn the way. If any of these situations sound acquainted, it’s time to take motion. Start by deleting any apps or games you didn’t download, erasing risky messages, and operating cellular safety software, in case you have it. Warn your contacts that your phone has been compromised, and to disregard any suspicious hyperlinks or messages coming from you. Malware may also be behind spammy pop-ups, changes to your home screen, or bookmarks to suspicious websites.
Dating & Romance Statistics
Those are clues that often mean the individual is trying to cover their true id. Fakers often pose as army members who’re serving overseas, which would seem to explain why they can not meet in person.


